Our Terms & Conditions | Our Privacy Policy
Intel Websites Exploited to Hack Every Intel Employee and View Confidential Data
By removing the search filter from the API request, the system returned a nearly 1 GB JSON file containing the names, job roles, managers, phone numbers, and mailbox addresses for Intel’s entire global workforce.
.webp.jpeg) Hierarchy Owners
Hierarchy Owners
This pattern of lax security was repeated across other internal systems. A “Product Hierarchy” management website contained hardcoded credentials for its backend services.
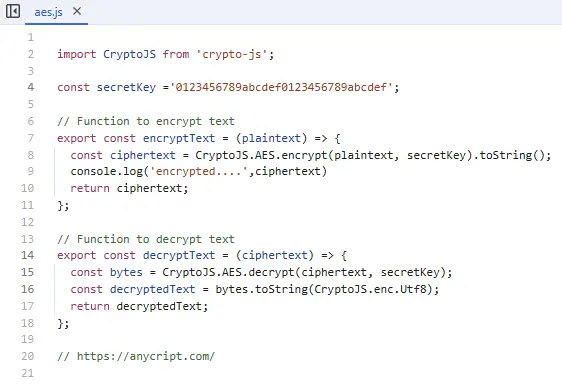
The password, while encrypted, used a notoriously weak AES key—’1234567890123456’—making it trivial to decrypt. This provided a second method to access the same employee database, Eaton Works said.
 Encryption
Encryption
Another “Product Onboarding” site, presumed to be used for managing entries on Intel’s public ARK product database, contained a trove of hardcoded secrets, including multiple API keys and even a GitHub personal access token.
The fourth major vulnerability was found in Intel’s Supplier EHS IP Management System (SEIMS), a portal for managing intellectual property with suppliers. The researcher bypassed the login by modifying the code that checked for a valid token.
From there, they gained administrative access by manipulating API responses, allowing them to view confidential supplier data, including details of non-disclosure agreements (NDAs).
Shockingly, the system’s backend APIs accepted a fabricated authorization token with the value “Not Autorized”—a typo that highlighted a complete breakdown in server-side security checks.
The researcher responsibly disclosed all findings to Intel beginning on October 14, 2024. The company’s bug bounty program policy excludes web infrastructure from monetary rewards, directing such reports to a security email inbox.
While the researcher received only an automated reply and no direct communication, they confirmed that Intel remediated all the reported vulnerabilities before the standard 90-day disclosure period ended.
.webp.jpeg) Email response
Email response
While no highly sensitive data like social security numbers or salaries were exposed, the breach of employee PII and confidential partner data on such a massive scale represents a significant security lapse for the technology giant.
Safely detonate suspicious files to uncover threats, enrich your investigations, and cut incident response time. Start with an ANYRUN sandbox trial →
Images are for reference only.Images and contents gathered automatic from google or 3rd party sources.All rights on the images and contents are with their legal original owners.


Comments are closed.